What Protection Does Webroot Provide For Datasheets? - www.webroot.com/safe
Sensitive data will be constantly at risk of theft, loss, and exposure. There are so many times, the data will walk simply right out the front door on the USB or laptop devices. Companies that suffer like data loss risk serious cons that include regulatory penalties, brand damage, public disclosure, customer distrust as well as financial loss. www.webroot.com/safe
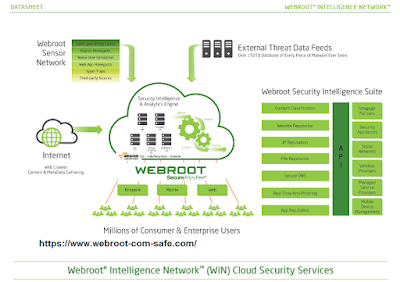 The rapid proliferation of mobile devices with wide storage capacities and often internet access is opening even more channels for data theft or loss. Hence, it is advisable to protect sensitive, personally identifiable, and proprietary details must be a top priority. Webroot provides advanced protection to the datasheet and we are here with a shot and quick guide about it.
The rapid proliferation of mobile devices with wide storage capacities and often internet access is opening even more channels for data theft or loss. Hence, it is advisable to protect sensitive, personally identifiable, and proprietary details must be a top priority. Webroot provides advanced protection to the datasheet and we are here with a shot and quick guide about it.Webroot Antivirus: Comprehensive Data Protection Suites
Webroot antivirus software addresses all of these concerns and also does a lot of work to protect datasheets. Data Sheets Managements of Native encryption management of native encryption will allow the customers to manage the native encryption functions that are offered by the Apple FileVault on OS X and MS BitLocker on the Windows platforms that are directly from Webroot policy software.
Management of native encryption hence provides zero-day compatibility with the Apple OS X and MS Windows patches, firmware updates, and upgrades from Apple and Microsoft, and zero-day assistance for new hardware from Apple.
Centralized Security Management and sophisticated reporting Utilize the centralized Webroot software console to enforce by implementing mandatory, company-wide security policies monitor the data encryption, monitor, and secure from the loss. Centrally define, manage, deploy, and update security policies that filter, monitor, encrypt, and block unauthorized access to private data. www.webroot.com/safe
Webroot Complete Data Security Features Enterprise-Grade Drive Encryption-
Automatically encrypt whole devices without the need of user action or training as well as impacting system resources
- Verified and checks authorized and legitimate users by using multifactor authentication
- Compatible with third-party credential providers
- In-place upgrade the support for Windows 10 Update Removable media encryption
- Automatic, on-the-fly encryption for virtually or any mobile storage device, company issue or not
- Encrypt or block writes to the removable media at the VDI Workstations
Access encrypted data from anywhere and without need for any extra software installation or the local administrative rights on the host device
Data Sheet
File, Folder, and Cloud Storage Encryption-
- Keep files and folders safe and secure wherever they are saved that includes local hard disks, removable media, file servers, and cloud storage like Box, Dropbox, MS OneDrive, and Google Drive
Manage Native Encryption On Macs And Windows
- Manage BitLocker on Windows 7, 8, and 10 systems directly from Webroot Software, without the requirement for a separate MS BitLocker Management and Administration server
- Report the Compliance in several reports and dashboards in Webroot software
Centralized Management Console
Use the Webroot software infrastructure management for the file, folder, and full-disk management and removable media encryption and control policy and patch management and retrieve lost passwords and demonstrate regulatory compliance.
- Synchronize security policies with the MS Active Directory, PKI, Novell NDS, and others
- Prove devices are successfully encrypted with the wide auditing capabilities
- Log the data transaction record like information as recipient, sender, timestamp, data, and time, and data evidence of the last successful login, date and time the last update received, and whether the encryption was successful.
Modify the Method for Data Security
Data security has always been an object of serious attention by enterprise protection executives and compliance officers, but the GDPR will elevate data protection undoubtedly to the boardroom because of the potential cons seriousness of noncompliance. webroot.com/safe
GDPR comes with an excellent chance for your C-Level executives to indulge with a legitimate advisor such as Webroot to discuss the recent business initiatives and to strategize your GDPR protection transformation. GDPR compliance will need more than basic data loss prevention and it also demands a risk-based approach of data security that will define the appropriate controls required to secure the vital information of the European citizens, streamline compliance procedures and achieve positive outcomes.
Webroot Cloud Data Security
With the dissolution of the corporate network perimeter, and gain visibility and also control the cloud and it is in everyone’s mind nowadays. Securing data that traverses the cloud is the main concern and store data without encryption and lack of multifactor authentication to access cloud services.
Webroot Addresses The Priorities Of Data Security
You should begin from the assess your data loss risks and then, take a list of your attack surfaces and then, look for a better way to secure them. You will need to think about the technology changes which might be embedded with a GDPR protection investment to provide security for personal data.
In GDPR Response, Webroot actually helps and accelerates the security changes around the whole data security lifecycle in an automated and integrated manner which lessens the skills and complexity burden. Webroot will protect you for the long term and provides excellent security and performance to your device. It will also help you with building a stronger security culture and archives innovative security maturity. webroot.com/safe

